
Set Up DKIM (DomainKeys) With Postfix On Ubuntu 20.04 LTS
It provides the steps to set up the DKIM i.e. DomainKeys with Postfix on Ubuntu 20.04 LTS for single domain and multiple domains.
As part of the anti-spam automation, the email administrators should include automated techniques including Sender Policy Framework (SPF), Domain-based Message Authentication, Reporting & Conformance (DMARC), and DomainKeys Identified Mail (DKIM) as part of the email server set up. The domain name owners must authorize their emails by updating the DNS. DKIM is an email authentication method to detect the forged sender addresses in emails to prevent phishing and email spam. The email server configured for DKIM signs the header fields and includes the digital signature in the header field of the outgoing emails. The From: header field must be signed by the appropriate signing module. The recipient email system can verify the digital signature linked to the domain name by looking up the DNS record of the sender domain having the sender's public key.
This tutorial provides the steps to install OpenDKIM on Ubuntu 20.04 LTS and configure it for Postfix to sign the header fields of the outgoing emails. I have used the domain example.com for demonstration purposes.
Prerequisites
It assumes that Postfix is already installed and the email server is working fine to send the emails. You may also refer Install Mail Server On Ubuntu 20.04 LTS Using Postfix, Dovecot, and Roundcube.
Install OpenDKIM
This section provides the commands to install OpenDKIM on Ubuntu as shown below.
# Install OpenDKIM
sudo apt install opendkim opendkim-tools
# Output
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following additional packages will be installed:
dns-root-data libmemcached11 libmilter1.0.1 libopendbx1 libopendbx1-sqlite3 libopendkim11 librbl1 libunbound8 libvbr2
Suggested packages:
unbound
The following NEW packages will be installed:
dns-root-data libmemcached11 libmilter1.0.1 libopendbx1 libopendbx1-sqlite3 libopendkim11 librbl1 libunbound8 libvbr2 opendkim opendkim-tools
----
----
Setting up opendkim-tools (2.11.0~beta2-1) ...
Setting up opendkim (2.11.0~beta2-1) ...
Created symlink /etc/systemd/system/multi-user.target.wants/opendkim.service → /lib/systemd/system/opendkim.service.
Processing triggers for systemd (245.4-4ubuntu3.1) ...
Processing triggers for man-db (2.9.1-1) ...
Processing triggers for libc-bin (2.31-0ubuntu9) ...
Configure OpenDKIM and Postfix
This section provides the steps to set up the email server for DomainKeys Identified Mail (DKIM) by configuring OpenDKIM and Postfix.
Configure OpenDKIM as shown below.
# Configure OpenDKIM
sudo nano /etc/default/opendkim
# Comment out
#SOCKET=local:$RUNDIR/opendkim.sock
# Add at last
SOCKET="inet:8891@localhost"
# Save and exit the editor
# Configure OpenDKIM
sudo nano /etc/opendkim.conf
# Add at the last
SOCKET inet:8891@localhost
# Save and exit the editor - Ctrl + o -> Enter -> Ctrl + x
Also, configure Postfix by updating it's main configuration file as shown below.
# Configure Postfix Main
sudo nano /etc/postfix/main.cf
# Add at the last
# DKIM
# -----------------------
milter_protocol = 6
milter_default_action = accept
smtpd_milters = inet:localhost:8891
non_smtpd_milters = inet:localhost:8891
# Save and exit the editor - Ctrl + o -> Enter -> Ctrl + x
In case you have installed Amavis, also update the master configuration of Postfix as shown below.
# Configure Postfix Master
sudo nano /etc/postfix/master.cf
# Udpate
-----
-o smtpd_client_connection_count_limit=0
-o smtpd_client_connection_rate_limit=0
-o receive_override_options=no_header_body_checks,no_unknown_recipient_checks,no_milters
-----
Generate Private Key - Single Domain
This section provides the steps to generate the private key for a single domain. The private key will be used to sign outgoing emails. We can configure OpenDKIM by adding the domain-specific configurations as shown below. I have used the selector dkim to configure OpenDKIM and DNS.
Configure OpenDKIM for example.com as shown below.
# Update OpenDKIM Conf
sudo nano /etc/opendkim.conf
# Add at the last
Domain example.com
KeyFile /etc/postfix/dkim.key
Selector dkim
# Save and exit the editor - Ctrl + o -> Enter -> Ctrl + x
We can generate the private key and the entry for the DNS record as shown below. It will generate the two files i.e. dkim.private and dkim.txt.
# Generate private key and dns record
sudo opendkim-genkey -t -s dkim -d example.com
Now deploy the private key to Postfix as shown below.
# Deploy the key to Postfix
mv dkim.private /etc/postfix/dkim.key
chmod 660 /etc/postfix/dkim.key
chown root:opendkim /etc/postfix/dkim.key
Also, restart Postfix and OpenDKIM to apply the changes.
# Restart OpenDKIM
service opendkim start
# Restart Postfix
service postfix restart
This completes the configuration part. Now the email server will sign headers of outgoing emails for the domain example.com. We are also required to update the DNS record as shown below.
# Read DKIM record
sudo cat dkim.txt
# Output
dkim._domainkey IN TXT ( "v=DKIM1; h=sha256; k=rsa; t=y; "
"p=KAABIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA/fedRNEFQvCdtN0akUCMG686J7Kv7DfjP6CBNYbq0zppCF+gEnXmeRIAG1BNGtqE0DnpiOaePwXpuAC+izWHE4pBltSwczhTOz7dNHxQV3YmPs3pg12Zqm4ARuD9sCdJky/Tz+uPHUYp8GUuAJPOmqmg3lWw9AooPOYfJMLte5BeQ7KtSiyxirT5VfZdYj0VJXvvlIKT8X92OY"
"WN8G0212XiFLyyQuxJixQL04BMG0bvBW8xrNDiNuiAkDGea/nUxKRMnuVKOvAa5JAhi/hNikCOP9NCibllwZLlS2E94bY9FVw+ymbBt0f4MMn/Y2LBLfEhLZq0AAx0KXkpPpkWbQIDLSRP" ) ; ----- DKIM key dkim for example.com
Remove all the double quotes and generate a single line record as shown below.
# Valid DKIM
v=DKIM1;p=KAABIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA/fedRNEFQvCdtN0akUCMG686J7Kv7DfjP6CBNYbq0zppCF+gEnXmeRIAG1BNGtqE0DnpiOaePwXpuAC+izWHE4pBltSwczhTOz7dNHxQV3YmPs3pg12Zqm4ARuD9sCdJky/Tz+uPHUYp8GUuAJPOmqmg3lWw9AooPOYfJMLte5BeQ7KtSiyxirT5VfZdYj0VJXvvlIKT8X92OYWN8G0212XiFLyyQuxJixQL04BMG0bvBW8xrNDiNuiAkDGea/nUxKRMnuVKOvAa5JAhi/hNikCOP9NCibllwZLlS2E94bY9FVw+ymbBt0f4MMn/Y2LBLfEhLZq0AAx0KXkpPpkWbQIDLSRP
Update the DNS by adding a TXT record as shown below.
Name Type Value TTL
dkim._domainkey.example.com. TXT "single line record" 300
This completes the DKIM configuration for example.com. We can also verify the DKIM record using the keycheck utility. Paste your DKIM record to the Key record text area and click the Check Button. It should successfully verify your DKIM record as shown in Fig 1.
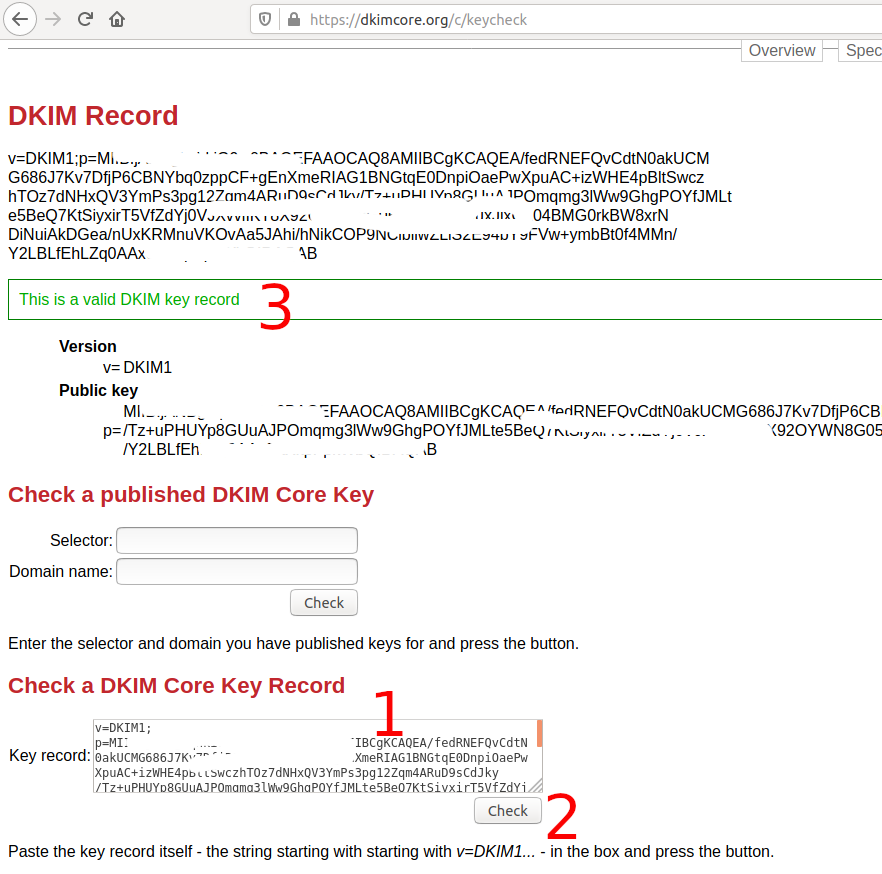
Fig 1
We can also use dig to check the DNS record as shown below.
# Dig
dig dkim._domainkey.example.com txt
# Output
; <<>> DiG 9.11.3-1ubuntu1.12-Ubuntu <<>> dkim._domainkey.example.com txt
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 8185
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;dkim._domainkey.example.com. IN TXT
;; ANSWER SECTION:
dkim._domainkey.example.com. 5 IN TXT "v=DKIM1;p=KAABIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA/fedRNEFQvCdtN0akUCMG686J7Kv7DfjP6CBNYbq0zppCF+gEnXmeRIAG1BNGtqE0DnpiOaePwXpuAC+izWHE4pBltSwczhTOz7dNHxQV3YmPs3pg12Zqm4ARuD9sCdJky/Tz+uPHUYp8GUuAJPOmqmg3lWw9AooPOYfJMLte5BeQ7KtSiyxirT5VfZdYj0VJXvvlIKT8X92OYWN8G0212XiFLyyQuxJixQL04BMG0bvBW8xrNDiNuiAkDGea/nUxKRMnuVKOvAa5JAhi/hNikCOP9NCibllwZLlS2E94bY9FVw+ymbBt0f4MMn/Y2LBLfEhLZq0AAx0KXkpPpkWbQIDLSRP"
;; Query time: 83 msec
;; SERVER: 127.0.0.53#53(127.0.0.53)
;; WHEN: Thu Jul 02 08:50:33 IST 2020
;; MSG SIZE rcvd: 479
Generate Private Key - Multiple Domains
This section provides the steps to configure multiple domains for OpenDKIM. The easiest approach is to simply use the wildcard as shown below.
# Update OpenDKIM Conf
sudo nano /etc/opendkim.conf
# Add at the last
Domain *
KeyFile /etc/postfix/dkim.key
Selector dkim
# Save and exit the editor - Ctrl + o -> Enter -> Ctrl + x
Also, restart Postfix and OpenDKIM to apply the changes.
# Restart OpenDKIM
service opendkim start
# Restart Postfix
service postfix restart
DKIM Test
We can perform the DKIM testing using DKIM Test. Now click the Next Step Button after opening the DKIM Test webpage. It will generate the endpoint to receive the email. Now send an email to this endpoint using the domain to be tested. It should successfully pass the DKIM test as shown in Fig 2.
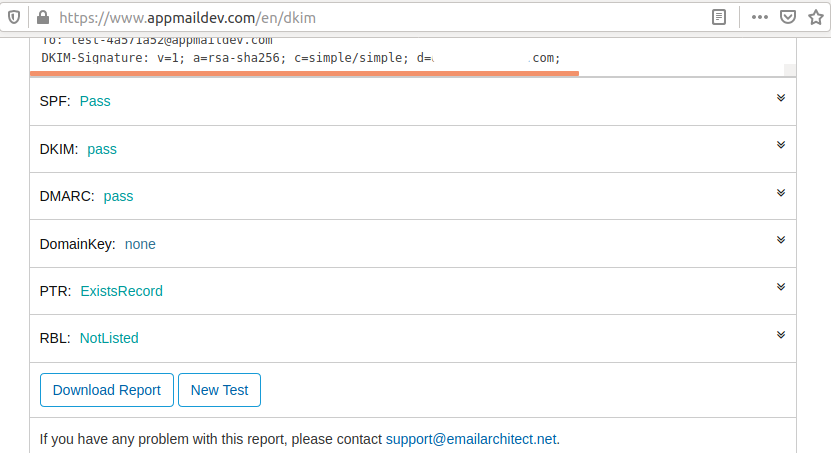
Fig 2
Now send an email to Gmail and check the Mailed By and Signed By parameters as shown in Fig 3.
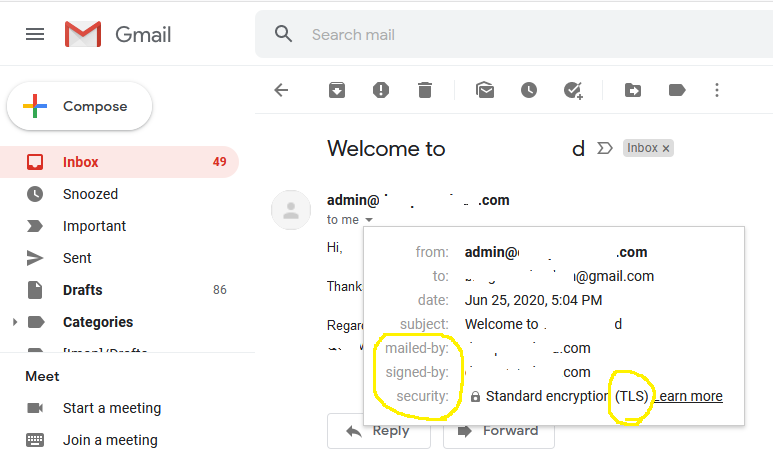
Fig 3
This ensures that your emails are properly signed by your domain.
Summary
This tutorial provided the steps to install OpenDKIM on Ubuntu 20.04 LTS. It also showed how to configure the OpenDKIM and Postfix to sign the outgoing emails and configure the DNS record.





